Assure Security
Comply with cybersecurity regulations and strengthen IBM i security
The IBM i platform is a key component of your IT infrastructure. Strengthen and integrate IBM i security into overall enterprise security for comprehensive business protection.
Assure Security delivers market-leading IBM i security capabilities that help your organization establish and automate effective, comprehensive, and auditable security practices.
Benefits
Prevent breaches
Detect, block and alert on unauthorized access while automating control of system authority levels and privileged accounts management
Automate and integrate security controls
Establish and maintain constant, enterprise-wide visibility into security policy compliance and ensure the integrity of regulated data
Protect privacy
Protect against theft and exposure of customer, partner, and employee data with state-of-the-art encryption and anonymization technologies
Defend against malware and ransomware
Deploy robust, multi-layered, and resilient defenses to protect your business against advanced threats
Assure Access Control
Enforce strict security policies to protect your systems and data with effective, automated control over every level and method of access.
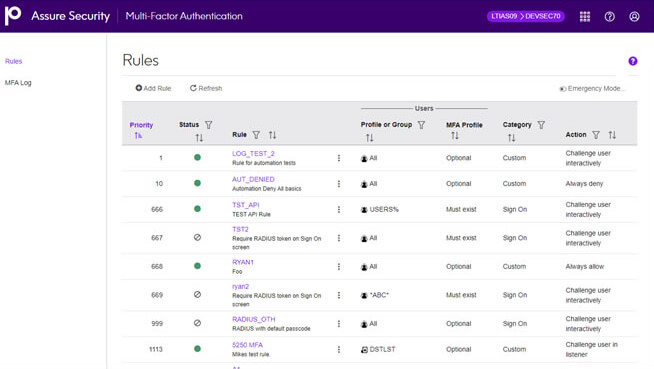
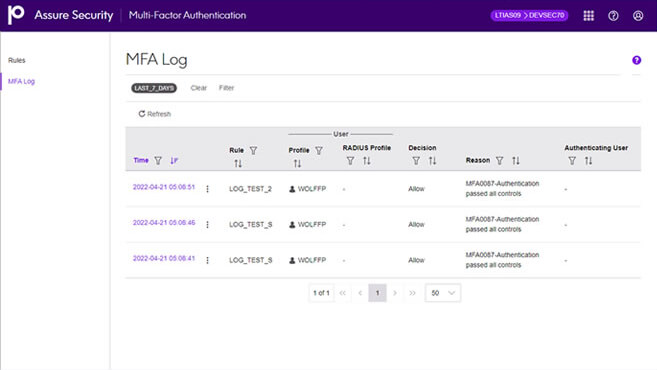
Multi-Factor Authentication strengthens logon security for configured users. Certified for RSA SecurID, Assure Multi-Factor Authentication also supports RADIUS servers or a Precisely-provided authenticator.
Elevated Authority Manager automatically controls and manages granting higher levels of user authority on an as-needed and time-limited basis, while comprehensively monitoring the actions of elevated profiles. Flexible, highly customizable rules define the context in which authority can be granted and the method to be used for elevating authority.
System Access Manager enables tight, automated control of all entry points and pathways into IBM i systems, including network protocols, communications ports, database protocols, and command lines. Granular rules control access based on user profile settings, date and time, IP address and more.
“Assure System Access Manager and Assure Monitoring and Reporting allowed us to achieve a high safety standard and meet several internal and external audit and regulation requirements.”
Cristian Guerra, Operational Risk Manager and Information Security
Assure Monitoring and Reporting
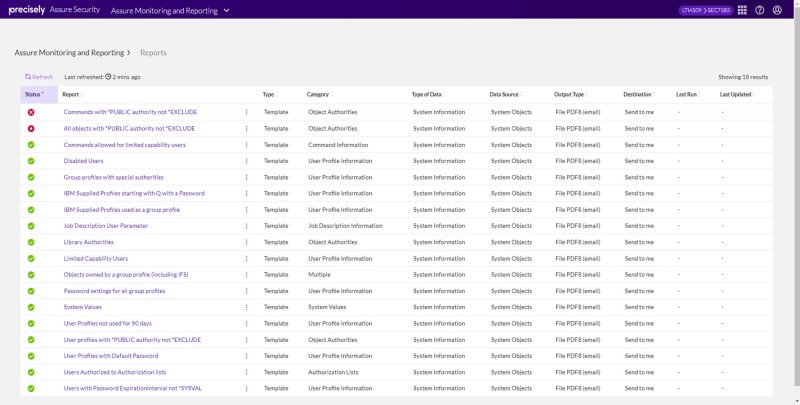
Establish and automate deep, continuous visibility into security issues and generate clear, actionable alerts and reports on IBM i system activity, database changes and views of Db2 data.
Monitoring and Reporting seamlessly extracts insights from IBM i journal data and delivers alerts and reports on security incidents and compliance deviations. Seamlessly integrate the full range of advanced IBM i security capabilities into your enterprise SIEM solution complete, fully coordinated, security.
Data Access Manager controls and monitors views of highly confidential Db2 data, ensuring the security of your most valuable corporate data while meeting the most stringent regulatory requirements for data confidentiality.
Assure Monitoring and Reporting
Assure Security
Security Risk Assessment
Security Assessment
Compliance Monitoring
Monitoring and Reporting
Db2 Monitor
Access
Control
Multi-Factor Authentication
Elevated Authority Manager
System Access Manager
Data
Privacy
Encryption
Secure File Transfer
Core Distribution Services
Assure Security delivers market-leading IBM i security capabilities that help your organization successfully comply with cybersecurity regulations.
Assure Data Privacy
Protect sensitive and highly regulated data from unauthorized access using advanced, state-of-the-art encryption, tokenization and masking technologies.
Encryption defends data at-rest using NIST-certified AES encryption for IBM i. It fully supports FIPS 140-2 compliant key managers as well as many leading OASIS KMIP-compliant key managers.
Assure Encryption also offers built-in masking and data access auditing, using rules-based definitions to automatically control which users can view unencrypted data, which can only view masked data (first 6, last 4, etc.), and which users are not allowed to view the information at all. Its extensive tokenization capabilities help maintain strict data privacy by temporarily or permanently replacing sensitive data with token values.
Secure File Transfer shields data moving across networks from view and automates transfers. Files are encrypted for transfer using globally recognized standard protocols including Secure Shell (SSH SFTP) and Secure FTP (SSL FTPS). Optional PGP encryption further protects data both at the source and destination.
“Assure Monitoring and Reporting now saves us countless hours when we get audit requests that require going back to database journals. I use its query function to show me specific data from selected windows of time and within 30 minutes I have a nicely formatted PDF report delivered to the department head.”
Rocky Marquiss, Sr. Programmer Analyst
Campbell County, Wyoming
Assure Malware Defense
The ever-escalating threats to your business posed by malware, and especially ransomware, cannot be ignored. Cyber-criminals are employing every technology and tactic available to defeat your security systems and then go completely unnoticed as they do unprecedented levels of damage. Countering them likewise requires deploying every possible method and tool you have available to build a coordinated and multi-layered defense. By combining the advanced capabilities available in Assure Security solutions, you can build a robust and resilient IBM i defense against malware and integrate it with your existing SIEM solution for even more comprehensive protection.
Defend against breach from without and within
Block unauthorized entry using Multi-Factor Authentication and then maintain strong cyber-checkpoints at every juncture with System Access Manager. Add Elevated Authority Manager to stop pretenders using fake or stolen credentials from getting into restricted systems and data while also ensuring that they can’t game the system to grant themselves higher levels of security clearance access.
Maintain constant vigilance
Leverage all the detailed security and operations data which is continuously maintained in the extensive array of IBM i journals and security logs. Use Assure Monitoring and Reporting to simplify extracting and presenting IBM i journal and log data for analysis and proof of regulatory compliance while integrating it all in real time with your existing SIEM solution’s alerting and reporting capabilities.
Make your data useless… to hackers
Cyber-criminals commonly use malware to obtain your data so they can get rich by reselling it or to achieve some other goal by publicly releasing it. But if all they can extract from your systems is data that is already encrypted, they have little leverage and no saleable merchandise.
Take all the resale value out of your data by using Assure Encryption to protect sensitive and highly-regulated data using advanced, state-of-the-art encryption, tokenization and masking technologies. Fully optimized for performance, Assure Encryption brings leading edge, NIST-certified AES encryption capabilities to your IBM i platform. And it fully supports FIPS 140-2 compliant key managers and many other leading OASIS KMIP-compliant key managers.