
AES vs PGP Encryption: What is the Difference?

In the world of data security there are many different types of encryption, but arguably the two most common are AES and PGP. With so many three-letter acronyms in the technical landscape, it’s easy to get lost in data security conversations. So let’s catch up!
First, we’ll define both AES and PGP encryption, and then we’ll look at how they compare to each other.
What is AES encryption?
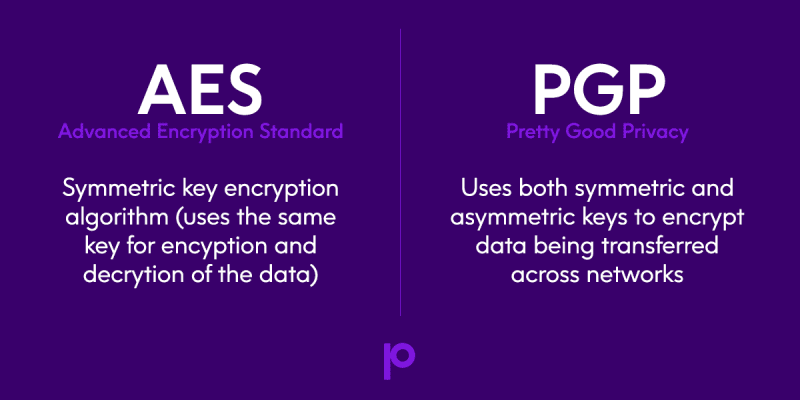
AES stands for Advanced Encryption Standard. It is the dreamchild of two cryptographers’ proposal of a symmetric key encryption algorithm based on the Rijndael cipher.
This algorithm was developed when the National Institute of Standards and Technology (NIST) sent the call out to the cryptographic community to develop a new standard. NIST spent five years evaluating 15 competing designs for the AES project. In 2001, NIST announced the cipher developed by the two Belgians, Joan Daemen and Vincent Rijmen, as the adopted standard (known as FIPS-197) for electronic data encryption.
AES is a symmetric key encryption algorithm, which essentially means that the same key is used to encrypt and decrypt the data.
A computer program takes clear text and processes it through an encryption key and returns ciphertext. If the data needs to be decrypted, the program processes it again with the same key and is able to reproduce the clear text. This method required less computational resources for the program to complete its cipher process, which means lower performance impact.
AES is a good method to protect sensitive data stored in large databases.
That said, AES will not always be your go-to for encrypting data.
When sharing sensitive information with trading partners or transferring information across networks, using AES would leave your data vulnerable because you would need to share your encryption key with your trading partners.
This means that while they would be able to decrypt the information you sent them, they could also decrypt anything else encrypted using that same key.
And if the key itself were compromised, then anyone in its possession could decrypt your data.
Read our eBook
IBM i Encryption 101
This eBook provides an introduction to encryption, including best practices for IBM i encryption.
What is PGP encryption?
The answer to your above data sharing security problem is found in PGP encryption. This is because PGP uses both symmetric and asymmetric keys to encrypt data being transferred across networks.
PGP stands for Pretty Good Privacy. Which is ironic because it’s actually much better than just “pretty good.”
PGP was developed by the American computer scientist Phil Zimmerman, who made it available for non-commercial use at no charge in 1991. To encrypt data, PGP generates a symmetric key to encrypt data which is protected by the asymmetric key.
Asymmetric encryption uses two different keys for the encryption and decryption processes of sensitive information. Both keys are derived from one another and created at the same time. This key pair is divided and referred to as a public key and a private key. Data is only encrypted with a public key, and thus, can only be decrypted with its matching private key.
PGP is just as strong as that of AES, but it adds an additional layer of security to prevent anyone who only has the public key from being able to decrypt data.
Another benefit of asymmetric encryption is that it allows for authentication. After you have exchanged public keys with your trading partners, the private keys can be used to digitally sign the encrypted content, allowing the decryptor to verify the authenticity of the sender.
PGP requires more computational resources, which is why it is usually not recommended for encrypting data in large databases where information needs to be accessed frequently, and each record that you access needs to be ran through a cryptographic process.
AES vs PGP: Which should I use?
When you are considering which encryption to use for your sensitive information, choose whichever will suit your needs best:
- AES is fast and works best in closed systems and large databases
- PGP should be used when sharing information across an open network, but it can be slower and works better for individual files.
For more information about data security for IBM i, read this eBook: IBM i Encryption 101


