IBM i Solutions
IBM i solutions
Help your organization successfully comply with security regulations, meet its needs for security auditing, and protect your business from planned and unplanned downtime in IBM i (AS/400) environments
IBM i security and availability challenges
Despite the inherent security capabilities of IBM i (AS/400), it isn’t without vulnerabilities. These security gaps can range from relatively common configuration issues to more complex and systematic concerns, but businesses must identify and rectify them to maintain the integrity of their IBM i platform. Even a single network intrusion can put organizational data and operability at risk.
Likewise, planned or unplanned IBM i downtime can come from any direction, in any form, at any time. Failure to keep a company operational during a server or disk failure, data center or site outage, or regional weather event, can cause irreversible damage to your business.
Use IBM i security and availability solutions from Precisely to handle regulatory compliance issues, stringent service level agreements, and provide unparalleled levels of data and systems availability.
Employees are either a company’s greatest assets in the fight against cyberthreats or its biggest liabilities. It is vital that IBM i (AS/400) users practice good cybersecurity hygiene, adhere to the latest best practices, and stay aware of the threat landscape.
Password management continues to be a major pain point for cybersecurity professionals. Some IBM i users continue to rely on their default login credentials to access their accounts, despite the significant threat this behavior poses to organizational integrity. Employees may even repurpose their username for their password, making it far easier for a malicious actor to access their account, get inside the IBM i system, and commit fraudulent activity.
It is also common for users to revert to default login credentials when requesting a password reset. Organizations must balance employees’ desire for convenience and streamlined access with the need for robust security procedures.
Multi-factor authentication (MFA) addresses password management pain points by requiring users to verify their identities using two or more criteria: something they know (e.g. password), something they have (e.g. mobile device) or something they are (e.g. biometric factors like fingerprints). With MFA, organizations are protected against a potential breach even if an external source acquires account login credentials.
The days when the IBM i was an isolated platform communicating through proprietary protocols are gone. Modern IBM i systems are highly connected through standard network and open-source protocols. This opens a wide variety of access points to the worldwide hacker community, who recognize the high value of data likely to reside on an IBM i.
Companies need to tightly control what their IBM i users have access to, what database changes they can make and what system changes they are authorized to perform. A perimeter must be drawn around the system to monitor every access point, including network connections, communication ports, database connections through open-source protocols, command execution, and more.
IBM i administrators need to find a way to have complete control of all entry points into their systems. They need granular control of access based on user profile settings, data and time, IP address, and other parameters. Every access attempt should be quickly and automatically reviewed, and either granted or denied according to access control policies.
Customers, business partners, and employees trust you to protect their confidential information from unauthorized access and theft. Any breach of that data would negatively impact relationships and your business’ reputation.
In addition to preventing theft of data by criminal intruders, internal staff, contractors, and business partners should only be allowed to see the specific data for which they are authorized access.
In fact, industry and state regulations such as PCI DSS, HIPAA, GDPR and more mandate the encryption of personally identifiable information (PII), payment card information (PCI), and personal health information (PHI).
Businesses have many options when it comes to strong protection for data that is both at rest and in motion, including encryption, tokenization, anonymization, and managed file transfer solutions. Encryption is a prerequisite for cybersecurity excellence, and it should be applied wherever personally identifiable or sensitive information needs to be protected from unauthorized access.
Encryption and key management solutions are available today that protect highly sensitive IBM i data at the field level, such as credit card information, without the need for application change and with minimal performance impact.
Laws change, threats evolve and no company can afford to be complacent when it comes to IT security and compliance. The only sensible path forward is to embrace a process of making continual improvements by regularly evaluating risk, hardening access, protecting confidential information, and monitoring activity.
Compliance requirements must be addressed in their entirety to protect an organization’s interests. Regulations such as GDPR, CCPA, HIPAA, and PCI DSS are often sweeping in their coverage and costly in their penalties.
Addressing every regulatory clause and requirement is difficult to achieve alone. Working with Precisely or a Precisely partner, companies can ensure their IBM i system complies with all relevant data privacy regulations and maintains compliance with the ever-expanding and increasingly complex list of data security regulations.
Security and compliance monitoring tools spot changes that deviate from compliance guidelines, impact particularly sensitive data, or exist outside the scope of accepted norms. Comprehensive audit trails ensure organizations can document system changes and demonstrate compliance to relevant regulatory bodies.
The field of cybersecurity is constantly evolving, with new vulnerabilities rapidly emerging and cybercriminals becoming more sophisticated with each passing year. It does not take long for cybersecurity best practices to become outdated.
Regulations often require annual IT risk assessments as a core requirement for compliance to ensure organizations stay ahead of evolving threats. However, not all security auditors are experienced with the nuances of IBM i, complicating the auditing process. Conversely, IBM i administrators may lack the time or expertise to conduct a thorough assessment of security standards and identify vulnerabilities. Businesses must also be careful to separate risk assessment duties, so the team responsible for administering the system is not also conducting audits and reviewing its own work.
Companies that infrequently execute risk assessments are effectively flying blind, unaware of where security gaps exist. Businesses should run risk assessments at a regular cadence – with the help of an expert consultant, if need be – to identify potential points of exposure and address security gaps before they lead to a costly data breach.
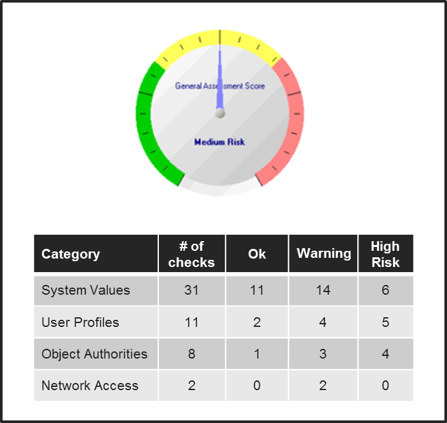
Learn how Assure Security Risk Assessment can help you identify vulnerabilities.
The pace and competitive landscape of global commerce necessitates a flexible, resilient, and available IT infrastructure that delivers 24×7 access to business-critical data and applications for customers, business partners and employees.
Any disruption to the availability of your business systems and data poses a threat to your business. Downtime not only impairs employee productivity; it impacts both short-term revenue through lost business and long-term revenue due to customer dissatisfaction. Moreover, it can tarnish your company’s reputation and harm its ability to win the trust of new partners and customers. Interruptions to business continuity, for even a short period of time, can seriously reduce your company’s profitability and possibly jeopardize its viability.
Achieving the levels of high availability required to support mission-critical systems puts increasing demands on IT professionals who need to meet their business’ increasing requirements for access to real-time data.
Layering security around systems and data
With the threat of cybercrime mounting, business decision-makers must make security a major priority. Because IBM i is one of the most securable operating systems available, organizations should seize every opportunity to use and expand upon its capabilities to prevent vulnerabilities. Perimeter defenses, system monitoring tools, advanced threat detection capabilities, compliance audits, and encryption are all essential in today’s cybersecurity environment. All organizations are at risk, regardless of their size, industry, or footprint.
Data breaches often have long-lasting effects, with victims requiring years to recover from the various financial losses, regulatory complications, and reputational damages. Robust cybersecurity hygiene remains a moving target as threats mature and grow increasingly sophisticated. It’s important that corporations never become complacent or lose sight of their cybersecurity goals.
It would be a mistake to assume that IBM i can handle all security concerns on its own without layers of security around the operating system. IBM i can establish a sound foundation for security, but it is in an organization’s best interest to build upon that foundation with additional layers of protection.
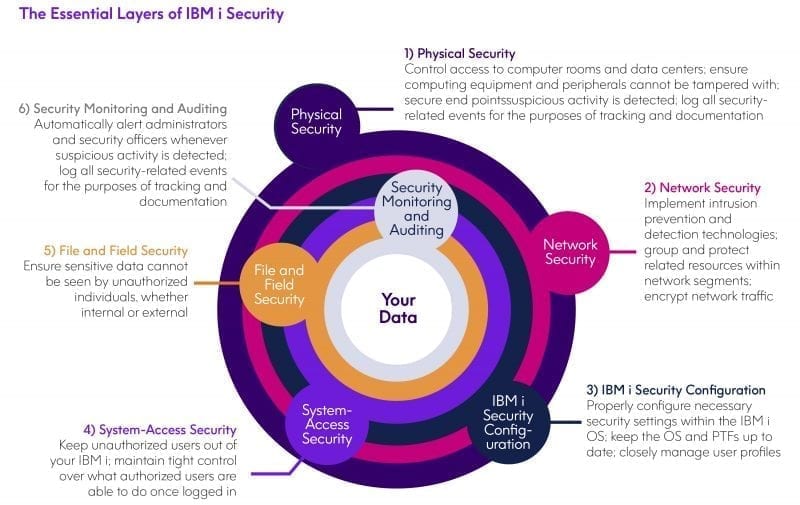
Read The Essential Layers of IBM i Security to learn more.
Integrating IBM i into a SIEM
Security Information and Event Management (SIEM) tools are in common use to provide a 360-degree view of IT operations and system security. SIEM solutions enable businesses to obtain greater visibility into the activities on their systems and more readily spot suspicious patterns that may indicate the presence of an unauthorized user or malicious actor.
Yet IBM i servers are not always integrated into that view. Even leading SIEM solutions such as IBM QRadar, LogRhythm, and Splunk do not natively integrate with IBM i.
Precisely’s security products seamlessly integrate IBM i security data into SIEM consoles to achieve more comprehensive visibility and incorporate IBM i security data into existing enterprise monitoring processes.
Assuring data availability and security
The continued popularity of the IBM i platform is a testament to the operating system’s longevity, transaction processing performance, and ability to run applications without change as new capabilities are added. Long-time adopters associate IBM i with reliability, and that reputation is certainly well-earned.
The demands for high availability and security are more stringent and vigorous than ever.
To ensure your systems and data stay secure and available, you need to analyze your needs against the available technologies and then look for a solution that will support your current needs as well as provide a growth path into the future. You need to leverage all your IBM i system’s powerful security features, wrap layers of security around the OS and its data, and integrate these processes and protocols with those protecting your other systems and networks. Fully and actively securing your IBM i platform is critical to keeping your entire business protected and is also necessary to achieve and prove regulatory compliance.